Phishing and identity theft
Identify and protect yourself against fake emails and websites that try to steal your credentials.
What is phishing?
A phishing attack is when someone deliberately tries to obtain your username and password to use them in a malicious way. These individuals want your username and password to send spam or more seriously infiltrate the University’s network. Do not be tricked into giving away your username or password.
Most phishing is conducted by email. Some attacks are pretty obvious. For example, "Your mail box is over quota, please reply to this email including your username and password to get more quota". Or you may be provided with a ‘link’ in an email that takes you to a form that asks for your username and password.
Protect your password
- You will never be asked for your password by University staff - all such requests are fraudulent.
- Never send your password in an email.
We do not enforce email quotas
- We will never tell you that your "email is almost full" or "you have reached your quota".
Be suspicious of:
- Any email that requires "immediate action" or creates a sense of urgency.
- Emails addressed to "Dear Customer" or some other generic salutation.
- Grammatical errors or spelling mistakes.
- Any link in an unsolicited email is suspicious, and it is even more suspicious if that link asks you to log in with your username and password. If there is any doubt, do not log in and contact the Student IT Hub (students) or the Staff Service Centre (staff).
Example of a phishing email
As an example of a phishing email, a number of students received an email claiming to be from 'EC Mail management', with the subject line 'Notification'. The text of the mail is as follows:
Dear User
To re-validate your mail account please click on the below link and enter your user id and password for maintenance and Virus Scanning, Very Important.
Click here
Your Mail account will be permanently terminatedin a short time for failure to adhere to our urgent notice.
Thank you for your cooperation.
EC MailManagement Support
© EC Services, ITS, The University of Auckland - All rights reserved.
A few characteristics give away that this is a good example of a phishing email. They are:
- The recipient is addressed as 'Dear User'. This email is sent by someone who has no idea who you are. The University, when it sends email to students, will know who you are, and will not use a 'Dear User' instead of your name.
- Incorrect capitals in the first sentence, the phrase 'Very Important' is capitalised and placed just before the 'Click here' link to provide a sense of urgency to click the link.
- The University does not need you to click on links to enable 'mail management and Virus Scanning'.
- Spelling errors. The space between 'terminated' and 'in' is missing.
- The use of phrases like 'failure to adhere to our urgent notice' is pretty characteristic of a phishing attempt.
- The mail is not signed by a person.
Make sure you're logging into the real University of Auckland login page
Cyber criminals will try to trick you into clicking on a link which takes you to a fake website that asks for your username and password. These websites may look legitimate. They might even look a identical to the University's login page.
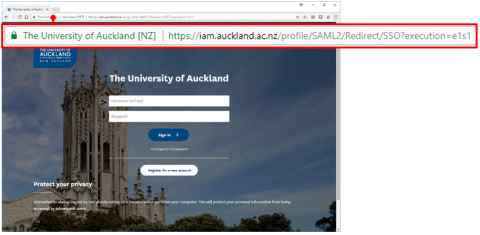
Always make sure that you're signing into the real University of Auckland login page by checking that:
- There is a padlock symbol in the browser location bar.
- The web address begins with "https://". The "s" stands for "secure" and means that your connection is encrypted.
- The web address on the login page is: https://iam.auckland.ac.nz/profile/SAML2/Redirect/SSO?execution=e1s1
- The site owner name "The University of Auckland [NZ]" is displayed in green in the location bar.
Below is an example of the University of Auckland's login page and the browser location bar.
What is identity theft?
Identity theft is when someone pretends to be someone else by assuming that person's identity, usually to gain access to resources such as your username, password, credit card and banking data.
There are a number of ways to do this from impersonating someone over the phone, stealing credentials through phishing to searching through your rubbish.
You can protect yourself by:
- Being alert to phishing attacks.
- Never sending credit card details over insecure channels such as email.
- Securing your desktop and mobile devices.
- Protecting sensitive data when disposing of computer equipment.